Here’s How Apple Has Responded to XARA Exploits
Last week, ‘XARA’ exploits, a.k.a ‘unauthorized cross-app resource access’ on Mac OS X and iOS, were disclosed to the public by researchers from Indiana University, Georgia Tech, and Peking University, claiming that Apple left millions of users vulnerable to unauthorized access to sensitive data such as iCloud passwords, authentication tokens, etc. Today, an Apple spokesperson has provided the following comment to iMore on the matter:
Earlier this week we implemented a server-side app security update that secures app data and blocks apps with sandbox configuration issues from the Mac App Store,” an Apple spokesperson told iMore. “We have additional fixes in progress and are working with the researchers to investigate the claims in their paper.”
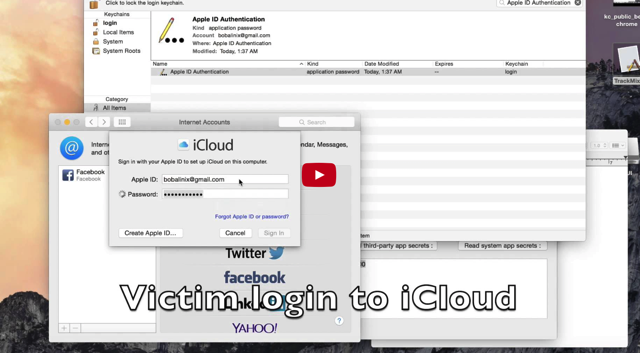
For those who aren’t aware, XARA targets the Keychain database on OS X where credentials are stored and exchanged; WebSockets, a communication channel between apps and associated services; and Bundle IDs, which uniquely identify sandboxed apps, and can be used to target data containers. On iOS, XARA targets URL schemes, which are used to move people and data between apps.
So while Apple continues to take measures against the range of XARA exploits for iOS and OS X, it’s best not to download software from any untrusted source or developer.

