
iPhone Unlocking Firm GrayKey Received Extortion Demands After Data Breach
A product made by Cellebrite competitor GrayKey is raising security concerns over a standalone device capable of unlocking iPhones.

Now, a recently suffered a data breach at the company allowed hackers access to a small portion of the GrayKey code, reports VICE‘s Motherboard.
The leaker is demanding 2 BTC or above from the company, roughly the same price as an entry level GrayKey. The leaker wrote the following message:
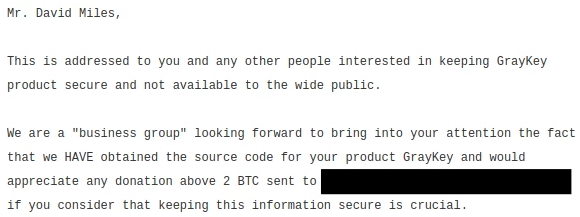
It’s assumed that the leaked code powers GrayKey’s user interface where messages are displayed. GrayShift confirmed the data breach and said in a statement to Motherboard that it occurred due to a “network misconfiguration at a customer site.”
GrayShift further said that no IP or data was exposed and they have made the necessary changes to prevent unauthorized access to their iPhone cracking devices.
According to Matthew Green, an assistant professor and cryptographer at the Johns Hopkins Information Security Institute, the device is capable of “bruteforcing” an iPhone with a six-digit passcode in an average of 11.1 hours, or up to 22.2 hours in a worst-case scenario.
The device can crack an iPhone with an 8-digit code in a few as 46 hours or up to 92 days, while the figures jump to 25 years, or 12 years on average, for strong 10-digit passcodes made up of random numbers.

