
Browser-Based Password Managers Are Being Exploited By Advertisers
Your browser’s built-in password manager could be exploited to share your email address with advertisers without your permission.

Nearly every web browser now comes with a password manager tool, a lightweight version of the same service offered by plugins like LastPass and 1Password. But according to new research from Princeton’s Center for Information Technology Policy, those same managers are being exploited as a way to track users from site to site.
The researchers have found that certain third-party scripts can be misused to steal identifiable data from these native password managers on these browsers.
“We found two scripts using this technique to extract email addresses from login managers on the websites which embed them. These addresses are then hashed and sent to one or more third-party servers. These scripts were present on 1110 of the Alexa top 1 million sites,” the researchers said.
On websites that have embedded either one of two tracking scripts – AdThink and OnAudience – the user is fed a second invisible login screen on a subsequent page that is autofilled by most browser password managers without the user realizing this is happening.
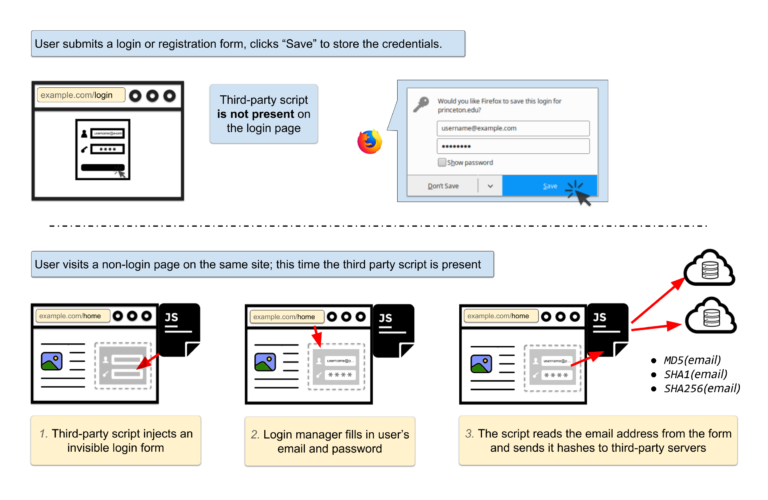
Fortunately, these third-party scripts have only been accessing emails and usernames.
“Why collect hashes of email addresses?,” reads the report. “Email addresses are unique and persistent, and thus the hash of an email address is an excellent tracking identifier. A user’s email address will almost never change — clearing cookies, using private browsing mode, or switching devices won’t prevent tracking.”
“The hash of an email address can be used to connect the pieces of an online profile scattered across different browsers, devices, and mobile apps. It can also serve as a link between browsing history profiles before and after cookie clears,” the researchers explained.
The plugins focus largely on the usernames and email addresses, but according to the researchers, there’s no technical measure to stop scripts from collecting passwords the same way. The only primary fix would be to change how password managers work, requiring more explicit approval before submitting information.
For users, this recent discovery only adds to the strong sense that ad tracking is running out of control in ways that can be extremely hard to keep tabs on. Tracking can be mitigated to some extent but only if users understand such a thing is necessary in the first place.

