Could Provisioning Profiles Be the Achilles Heel of iOS?
While there was a spike in Android malware, iOS has been a relatively secure mobile platform thanks to the app review process and app sandboxing. But it had its share of flaws, as the most recent reports have highlighted (see here and here). A security company, however, seems to be concerned about an iOS feature that could be the used by hackers to read information, passwords and even access encrypted data.
What feature of iOS has this potential to be the easily accessible door for malware? As the Skycure blog post emphasizes: Provisioning profiles.
iOS provisioning profiles, also know as mobileconfig files, are used by carriers, Mobile Device Management solutions and even mobile apps (like Hotspot Shield VPN) to configure key system-level settings of iOS devices. These profiles are usually used for constructive purposes, but the same capabilities can be explored and exploited by hackers to circumvent Apple’s security model.
To demonstrate the potential of Provisioning profiles, Skycure’s CTO Yair Amit and CEO Adi Sharabani sent Mathew Panzarino of The Next Web to a website where he tapped a link that presented him a provisioning profile. You may recall that some apps require this action as well. He then installed the profile with another tap and ended up with a screen that looks like this:
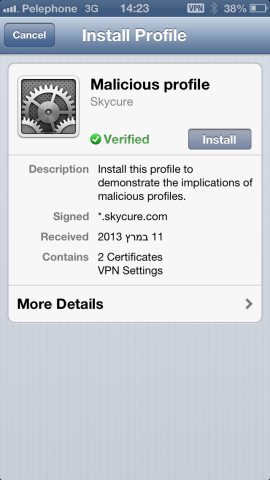
And now comes the most interesting part: After installing the profile, the sender was able to read which websites Mathew visited. Furthermore, he could scrape keystrokes, searches, and login data from apps like Facebook and LinkedIn.
How could this happen? The answer is in the power of provisioning profiles. These profiles are empowered to step outside the sandboxing protection offered by iOS by default, and thus can do things like routing all the victim’s traffic through a third-party server, installing root certificates, allowing for interception and decryption of secure HTTPS traffic, and much more.
Most alarmingly, with a malicious profile installed the hack can affect a user without his or her knowledge. This can only happen, however, if you have opted to install that provisioning profile in the first place.
The Skycure report goes even deeper: In a scenario presented by the company, when a carrier requires the user to install a special provisioning profile configuring a device to work with their network’s data server, the sites could be subject to a hack. The result: Corrupted profiles and users exploited while completely unaware.
But since there is no evidence of a provisioning profile attack, the above scenarios are just supposititious. Yet, they highlight the very real potential of these types of attacks.
They do, however, require your consent, as you will be prompted to install the provisioning profile first for the hacker to access your data. So what users can do is make sure the profiles they install are from trusted and verified sources.