Cryptographer Raises Security and Privacy Concerns Over iMessage
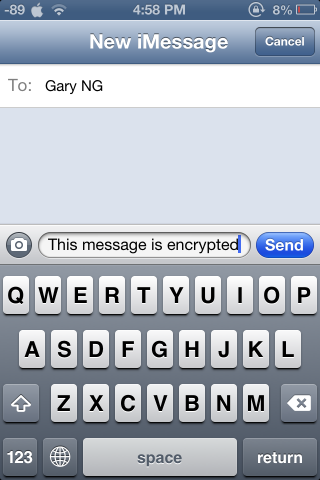
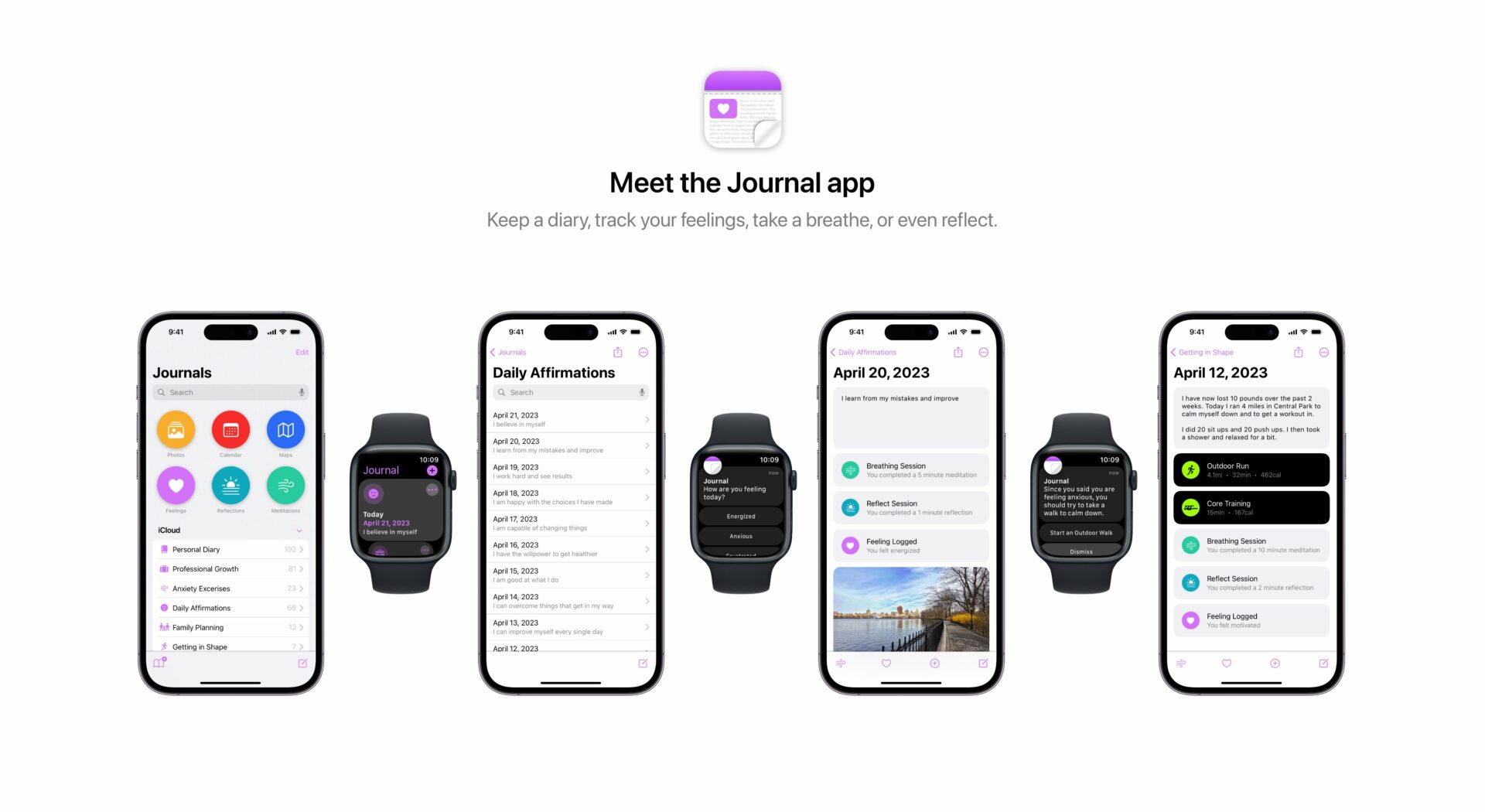
Apple claims that iMessage conversations use end-to-end encryption and as a result cannot be decrypted by the company. The statement was released in light of the PRISM scandal.
There are certain categories of information which we do not provide to law enforcement or any other group because we choose not to retain it.
For example, conversations which take place over iMessage and FaceTime are protected by end-to-end encryption so no one but the sender and receiver can see or read them. Apple cannot decrypt that data.
Mathew Green, a cryptographer and research professional at Johns Hopkins University, decided to investigate Apple’s claims (via iMore) and raised some important questions about these claims.
First, there is the iCloud backup. Green was using the iCloud backup service, to backup his iPhone and after losing the device, he was able to recover those messages. This obviously led to the question: how is Apple protecting iMessages?
Well, it certainly doesn’t protect them with the user’s password or with the device key.
And that is bad, because it means if Green could recover his messages with his brand new iPhone, someone at Apple could have also done it, possibly at the request of law enforcement.
Another important question Green raises is how does Apple distribute iMessage encryption keys. In order to understand the importance of this question, you need to know that in order to read an encrypted message you must possess the sender’s public key. Since you are not in a position to know who’s public key it is you are receiving to decrypt the message, there exists a possible scenario in which Apple could theoretically encrypt the messages with their own private key and send you their public key to decrypt. In other words, the content can be read by Apple in this scenario.
The main problem is that a third party could do the same.
Green also points out a most interesting fact: while Apple cannot read your messages, it is able to retain metadata since this data is delivered through its own servers. Metadata can be as valuable as the content itself.
However, this doesn’t mean you must stop using iMessage. Green’s post just highlights how Apple could easily decrypt communications sent through iMessage, which uses their own servers. His article is based on the little information available about how Apple secures these communications. He also urges the company to publish the technical details of iMessage encryption.