Apple Makes 2FA Text Codes Safer from Phishing Attacks
Image via MacWorld
According to MacWorld, Apple has implemented some modifications to the way the two-factor authentication (2FA) SMS autofill feature works on its devices.
Whenever a user receives a two-factor authentication SMS on their iPhone, the feature shows the 2FA code above the on-screen keyboard, allowing for a 1-tap paste, to save time.
However, phishing attackers have wised up to this feature (and other autofill technologies). When users are directed to a phishing link by attackers and the website sends them a 2FA security code via SMS, the autofill option showing up for the code often serves to make the website appear legit when it is actually not.
To prevent that from happening, Apple has introduced new layers of security to the feature, which now only offers to autofill a verification code if the domain of the website you’re on and the domain that sent the code match.
For example, if the site claims to be apple.com but the phishing link asking for the verification code is apple.securelogin.com, then the autofill option won’t be offered.
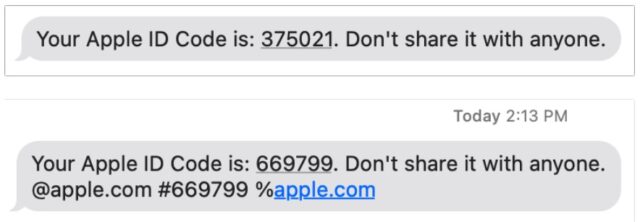
The iPhone maker is asking websites to start sending 2FA codes in the new, more secure format. Take a look at what the new format for 2FA SMS codes on Apple devices looks like:
Your Apple ID Code is: 123456. Don’t share it with anyone. @apple.com #123456 %apple.com
According to Macworld, the format is composed of:
- A standard human-readable message, including the code, followed by a new line.
- The scoped domain as
@domain.tld.- The code repeated again as
#123456.- If the site uses an embedded HTML element, called an iframe, the source of the iframe is listed after %, such as
%ecommerce.example. (The original spec specifies @; Apple appears to be using % for its texts.)
Apple explained changes were coming in August 2020 to developers.
“When you use a domain-bound code, AutoFill will suggest the code if — and only if — the domain is a match for the website or one of your app’s associated domains. For example, if you receive an SMS message that ends with @example.com #123456, AutoFill will offer to fill that code when they interact with example.com, any of its subdomains, or an app associated with example.com,” said Apple.
“If instead you receive an SMS message that ends with @example.net #123456, AutoFill will not offer the code on example.com or in example.com’s associated app. This makes it harder for an attacker to trick someone into entering one-time codes into a phishing site,” detailed the iPhone maker.
With these changes, the onus of responsibility falls upon users to notice when their device isn’t offering to autofill a received authentication code, and consequently proceed with caution.
SMS-based two-factor authentication is not the most secure, but it is certainly better than nothing. For a more reliable solution, consider using a 2FA code generator — one even comes built into iOS 15 and later.