
Security Researcher Discovers iCloud Access Vulnerability
A security researcher found a vulnerability allowing bad actors to brute force iCloud access.
The Zero Hack
After successfully discovering an Instagram account takeover vulnerability, security researcher Laxman Muthiyah from The Zero Hack realized that a number of other services are vulnerable to so-called “race hazard based brute force” attacks, including Apple.
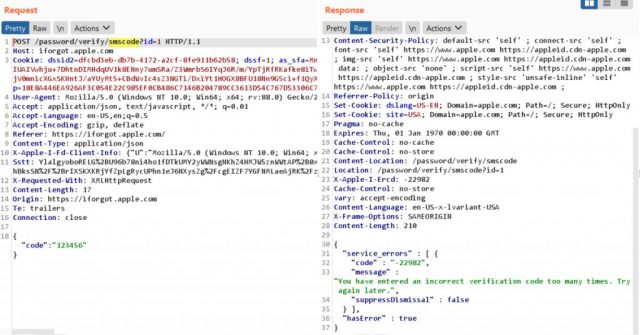
As such, Muthiyah took a turn trying to hack a vulnerability withing the “forgot password” option within the Apple ID service, requiring users to use a 6-digit OTP code and their email address.
In order to exploit the vulnerability, one needs to know a user’s trusted phone number as well as their email address to request the OTP code. One would then have to try all the possibilities of the 6 digit code, that would be around 1 million attempts (10 ^ 6).
However, after 5 attempts, the service locks users out, so Muthiyah did some testing. After the testing, he found a few things:
- iforgot.apple.com resolves to 6 IP addresses across the globe – (17.141.5.112, 17.32.194.36, 17.151.240.33, 17.151.240.1, 17.32.194.5, 17.111.105.243).
- There were two rate limits we have seen above, one is triggered when we send more than 5 requests to forgot password endpoint (http://iforgot.apple.com/password/verify/smscode) and another one is across the apple server when we send more than 6 concurrent POST requests.
- Both these rate limits are specific to apple server IP which means we can still send requests (with in limits though) to another apple server IP.
- We can send upto 6 concurrent requests to an apple server IP (by binding iforgot.apple.com to the IP) from single client IP address as per their limits. There are 6 apple IP address resolved as mentioned above. So we can send upto 36 requests across the 6 apple IP address (6 x 6 = 36) from single IP address.
- Therefore, the attacker would require 28K IP addresses to send up to 1 million requests to successfully verify the 6 digit code.
Read the entire explanation of the vulnerability over at The Zero Hack.

