
Proof of Concept of Apple’s “Gotofail” Exploit Developed in Less Than a Day
A New Zealand security consultant has developed a proof of concept of the currently open OS X security vulnerability known as “gotofail”, which was uncovered during the weekend (via ZDNET).
And on OSX, I have full interception of software update traffic. pic.twitter.com/v2BlWdWjyz
— Aldo Cortesi (@cortesi) February 25, 2014
After modifying his existing mitmproxy code, Aldo Cortesi managed to take advantage of the Mac OS X flaw, and he immediately penned a blog post detailing his findings.
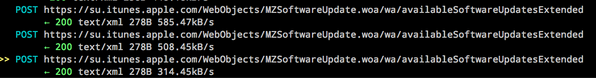
I’ve confirmed full transparent interception of HTTPS traffic on both IOS (prior to 7.0.6) and OSX Mavericks. Nearly all encrypted traffic, including usernames, passwords, and even Apple app updates can be captured. This includes:
– App store and software update traffic
– iCloud data, including KeyChain enrollment and updates
– Data from the Calendar and Reminders
– Find My Mac updates
– Traffic for applications that use certificate pinning, like Twitter
When contacted by ZDNET, Cortesi said that it took him less than a day to begin intercepting HTTPS traffic on both OS X Mavericks and iOS 7.05 and lower. Although he has posted screenshots to show his capture of software updates and iCloud keychain traffic, he has refused to release his proof of concept until Apple addresses the flaw.
As of writing this article, there is no software update available for Mavericks users. Security experts recommend users to stay away from untrusted networks and avoid Safari, which is more dependent on Apple’s implementation of SSL and TLS than other browsers such as Firefox and Chrome.

