
This Simple Exploit Can Bypass OS X’s Malware Gatekeeper
Patrick Wardle, director of research of security firm Synack, has found a very simple exploit that completely bypasses Mac’s Gatekeeper, an OS X feature that helps neutralize attacks that trick less experienced users into installing trojans and provides code-signing requirements to prevent installation of malicious software. According to ArsTechnica, the simple hack uses a binary file already trusted by Apple to pass through Gatekeeper, and executes one or more malicious files that are included in the same folder.
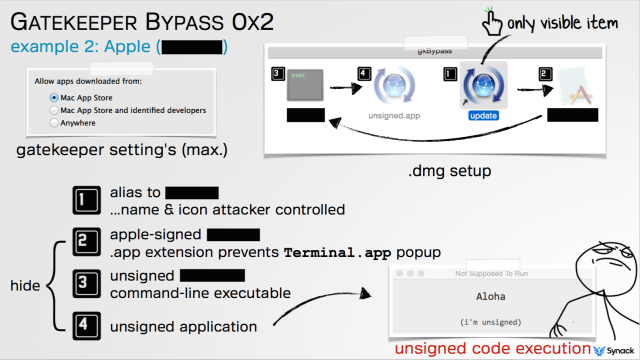
The source details that once the Apple-trusted file is on the other side, the bundled files can install a variety of malicious programs, including password loggers, apps that capture audio and video, among other malware. The security researcher notes that the bypass “stems from a key shortcoming in the design of Gatekeeper” rather than a defect in the way it operates. Gatekeeper’s sole function is to check the digital certificate of a downloaded app before it’s installed to see if it’s signed by an Apple-recognized developer or originated from the official Apple App Store.
Gatekeeper was never set up to prevent apps already trusted by OS X from running in unintended or malicious ways, as the proof-of-concept exploit he developed does. “If the application is valid—so it was signed by a developer ID or was (downloaded) from the Mac App Store—Gatekeeper basically says ‘OK, I’m going to let this run,’ and then Gatekeeper essentially exits,” Wardle told Ars. “It doesn’t monitor what that application is doing. If that application turns around and either loads or executes other content from the same directory… Gatekeeper does not examine those files.”
The researcher has revealed that he has alerted Apple officials to his discovery and believes they are working on a fix already.

