Vulnerability Allows Researcher to Completely Bypass macOS Gatekeeper Security
A new vulnerability highlighted in a blog post by security researcher Filippo Cavallarin, which continues to exist even in the latest macOS 10.14.5 release, allows a user to completely bypass the Gatekeeper security functionality of macOS, 9to5Mac is reporting.
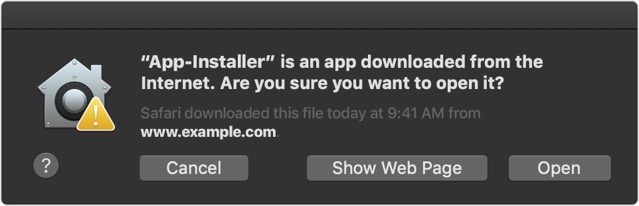
For those who aren’t familiar, macOS Gatekeeper verifies applications downloaded from outside of the Mac App Store immediately after they are downloaded, preventing them from being run without user consent. If the code has not been signed, the app won’t open without the user giving direct permission. According to Cavallarin, however, this functionality can be easily bypassed.
The researcher explains that in its current implementation, Gatekeeper considers both external drives and network shares as “safe locations,” meaning it allows any application contained in those locations to run without checking the code again:
To better understand how this exploit works, let’s consider the following scenario: An attacker crafts a zip file containing a symbolic link to an automount endpoint she/he controls (ex Documents -> /net/evil.com/Documents) and sends it to the victim.
The victim downloads the malicious archive, extracts it and follows the symlink.
Now the victim is in a location controlled by the attacker but trusted by Gatekeeper, so any attacker-controlled executable can be run without any warning. The way Finder is designed (ex hide .app extensions, hide full path from titlebar) makes this technique very effective and hard to spot.
Although Cavallarin informed Apple of this flaw on February 22nd, the company has not yet addressed the issue. He has, therefore, made the details of the flaw public today as the 90-day window he gave Apple has passed.