Pod2g Shows How Apple’s iMessage Can Be Decrypted on Camera [VIDEO]
Earlier this morning Apple responded to a previous story about its iMessage platform, saying the company cannot read your messages, based on researched revealed yesterday by Pod2g and his security firm QuarksLab at a conference in Kuala Lumpur, Malaysia. Looks like that statement was released too soon, as a newly released video shows a different story.
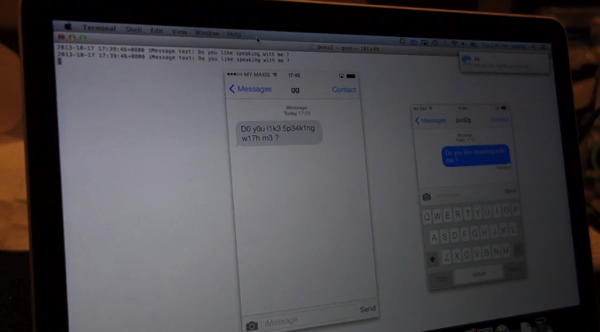
ZDNet, which attended the conference, now posts a video showing Pod2g demonstrating in real-time how iMessages were able to be decoded and read on the fly. Check it out below:
The hackers said any device that uses iMessage is affected and the team will release a fix for jailbroken iOS devices after the presentation:
“Basically, nearly all current Apple products: iMac, Mac Pro, MacBook Pro, MacBook Pro Retina, iPhone, iPod Touch, iPad. We will release a tweak for jailbroken iOS devices and an application for OS X just after the presentation.”
But regular consumers need not worry, as Pod2g and his team explains it’s a sophisticated hack that requires skill and physical control of your device at least once:
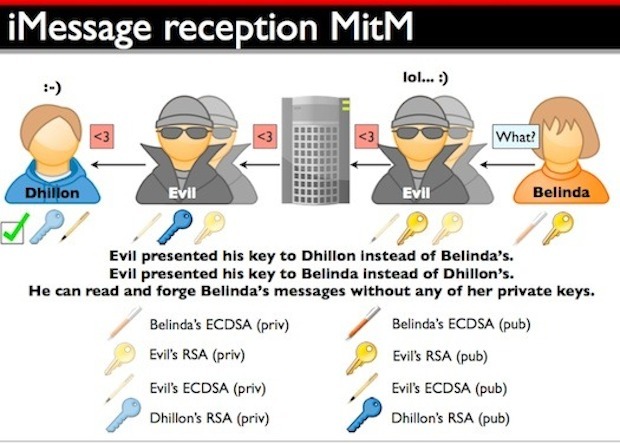
The researchers explained that to break iMessage encryption (AES, RSA, and ECDSA algorithms) in the manner shown would require the attacker to get physical control of the device — once.
Then, the attacker would install fraudulent certificates on it, and run spoofed servers tricked out to mimic Apple servers. The flaw’s essence, as QuarksLab described it, lies in the protocol’s lack of certificate pinning.
Even though performing this man-in-the-middle attack is quite a lot of work, and can only be done under limited circumstances, QuarksLab told the security conference’s attendees that if they needed a secure message system, they should choose a different one. Especially, they jokingly cautioned, if the messages contain discussion of Apple related zero-days or exploits
QuarksLab released a tool for skilled and advanced users with jailbroken devices called “iMTM Protect” to allow users to plug the iMessage flaw. You can read the entire QuarksLab security presentation here.
In summary, here’s what Pod2g and his team have to say about this iMessage flaw:
So, yes, there is end-to-end encryption as Apple claims, but the weakness is in the key infrastructure as it is controlled by Apple: they can change a key anytime they want, thus read the content of our iMessages.
The flaw, as stated will require considerable work for someone to hack your iMessages. The facts are this one was discovered by Pod2g but you can bet Apple is already working on fixing this security hole.