Apple Responds to ‘Backdoor’ Allegations in iOS Diagnostics Support Document
Apple has released a new support document which details iOS diagnostics capabilities, in what appears to be a response to claims by security researcher Jonathan Zdziarski that the company is aware of ‘backdoors’ in iOS.
The following three services are outlined by Apple in the same order they appeared in Zdiarski’s HOPE/X presentation slides, seemingly a sign the support document is a response to the allegations:
1. com.apple.mobile.pcapd
pcapd supports diagnostic packet capture from an iOS device to a trusted computer. This is useful for troubleshooting and diagnosing issues with apps on the device as well as enterprise VPN connections. You can find more information at developer.apple.com/library/ios/qa/qa1176.
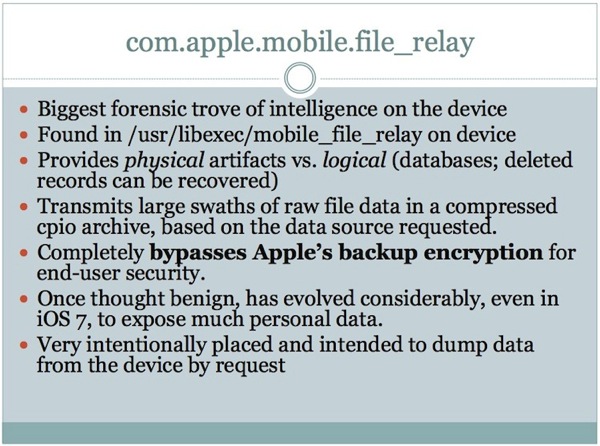
2. com.apple.mobile.file_relay
file_relay supports limited copying of diagnostic data from a device. This service is separate from user-generated backups, does not have access to all data on the device, and respects iOS Data Protection. Apple engineering uses file_relay on internal devices to qualify customer configurations. AppleCare, with user consent, can also use this tool to gather relevant diagnostic data from users’ devices.
3. com.apple.mobile.house_arrest
house_arrest is used by iTunes to transfer documents to and from an iOS device for apps that support this functionality. This is also used by Xcode to assist in the transfer of test data to a device while an app is in development.
You can see a preview of the slides Apple is referring to in its support document below:


Apple already released a statement declaring “As we have said before, Apple has never worked with any government agency from any country to create a backdoor in any of our products or services.”
