Hacker’s iOS Developer Account Shut Down After Malware Uploaded to App Store
In a story documented by Forbes, hacker Charlie Miller was able to upload a malware-infested app into the App Store:
At the SysCan conference in Taiwan next week, Miller plans to present a method that exploits a flaw in Apple’s restrictions on code signing on iOS devices, the security measure that allows only Apple-approved commands to run in an iPhone or iPad’s memory. Using his method–and Miller has already planted a sleeper app in Apple’s App Store to demonstrate the trick–an app can phone home to a remote computer that downloads new unapproved commands onto the device and executes them at will, including stealing the user’s photos, reading contacts, making the phone vibrate or play sounds, or otherwise repurposing normal iOS app functions for malicious ends
Video below:
Since his discovery of this major exploit in iOS, Apple has shut down Miller’s developer account and pulled his approved app from the App Store.
A former NSA analyst, Miller is one of the most highly skilled iPhone hackers, and has a knack for exploiting the device. Just this spring, he won the Pwn2Own conference here in Vancouver for a third year in a row for ‘pwning’ an iPhone 4 faster than anyone else.
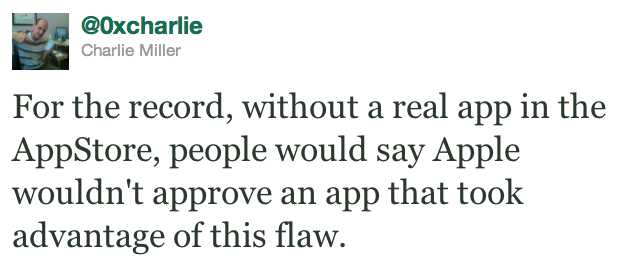
Miller just noted the following on twitter:
For the record, without a real app in the AppStore, people would say Apple wouldn’t approve an app that took advantage of this flaw.
Apple will most likely close this exploit when iOS 5.0.1 is released in a few weeks to address battery life issues. I’m not surprised Apple would pull his account, as he violated the terms of the developer account. Yet at the same time, he helped Apple address a massive security hole in iOS. I guess we can say Charlie ‘took one for the team’, eh?