New ‘XcodeGhost S’ Discovered to Target iOS 9 Users
A month after the biggest malware attack on the App Store and all the press around it, many US businesses are still using iOS apps infected with the XcodeGhost malware, reports mobile-security firm FireEye. Also, the “developer“ behind XcodeGhost has apparently found a way to get around Apple’s defence with a new version of the malware, dubbed as XcodeGhost S, which targets iOS 9 users (via PCWorld).
You may recall that last month more than 4,000 apps were identified as infected with the XcodeGhost malware — built using a counterfeit version of Xcode, Apple’s development tool. The problem with those apps was that they contained hidden code that was able to collect sensitive data about devices.
Apple reacted fast, and alongside removing the infected apps, it implemented additional levels of security. However, as FireEye found, many users are still running the older, infected versions of the apps on iOS devices; hence, XcodeGhost continues to represent a risk in the US and other markets.
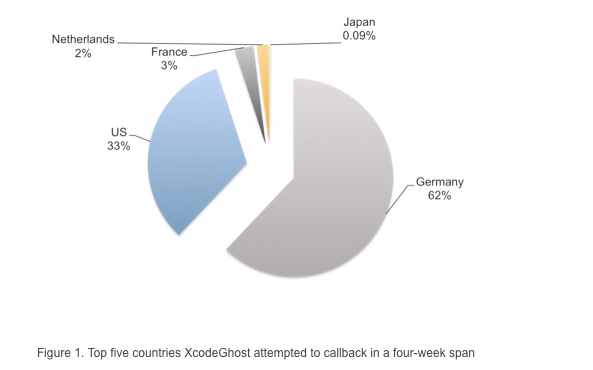
According to the security firm’s blog post, these apps are still trying to contact XcodeGhost’s command and control servers. Among the identified apps, we find the popular WeChat messaging app and a music app called Music 163.
The problem seems to be that the majority (close to 70%) of those devices — used in the enterprise — are still running older versions of iOS. As such, the firm recommends that they upgrade to iOS 9 as soon as possible.
Also, FireEye identified an application (a shopping app offered in China and the US, loosely translated as “Free State”) containing the modified version of the malware, XcodeGhost S. The firm worked with Apple to remove the app from the App Store.

