Android Contact Tracing App Contained Serious Privacy Flaw
Android’s contact tracing app reportedly contained a serious privacy flaw.
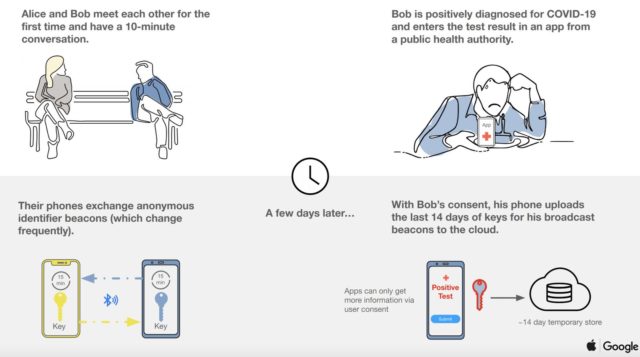
According to a new report from The Markup, the Android version of Google and Apple’s COVID-19 contact tracing app had a privacy flaw that let other preinstalled apps potentially see sensitive user data, including if someone had been in contact with a person who tested positive for COVID-19.
AppCensus first reported the vulnerability to Google in February, but the company failed to address it.
“This fix is a one-line thing where you remove a line that logs sensitive information to the system log. It doesn’t impact the program, it doesn’t change how it works,” said Joel Reardon, co-founder and forensics lead of AppCensus. “It’s such an obvious fix, and I was flabbergasted that it wasn’t seen as that.”
“We were notified of an issue where the Bluetooth identifiers were temporarily accessible to specific system level applications for debugging purposes, and we immediately started rolling out a fix to address this,” Google spokesperson José Castañeda said.
On Android phones, the contract tracing data is logged in privileged system memory, where it’s inaccessible to most software running on the phone. But apps that are preinstalled by manufacturers get special system privileges that would let them access those logs.
The problem is an implementation issue and not inherent to the exposure notification framework, Serge Egelman, the chief technology officer at AppCensus, said in a statement.
“We hope the lesson here is that getting privacy right is really hard, vulnerabilities will always be discovered in systems, but that it’s in everyone’s interest to work together to remediate these issues,” Egelman said.