
Cryptography Experts Says Apple Should Replace its iMessage Encryption Protocol
A team of researchers from Johns Hopkins University led by cryptography expert Matthew Green recently discovered several issues relating to Apple’s iMessage encryption. There findings were revealed at the Usenix Security Symposium.
The findings were immediately followed by Apple’s initiative to add a series of short and long-term defences to the iMessage protocol.
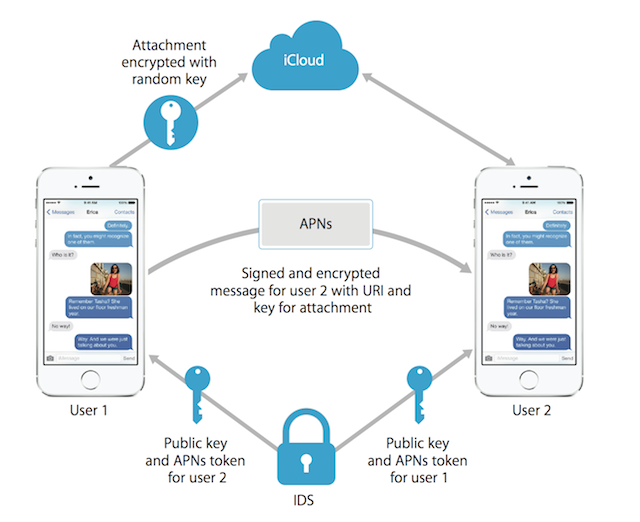
The team’s research was based on a ‘chosen cipher text attack’ on the iMessage encryption protocol. This allowed them to decrypt certain types of iMessage data and attachments while the sender or receiver was online. Although, it only worked on cipher texts containing gzip compressed data.
The researchers have named their attack the ‘Gzip Format Oracle Attack.’ According to them, this attack can be carried out anywhere but will require a high-level of technical expertise by the attacker.
The security experts also found several flaws in how iMessage handles device registration and key distribution. The researchers pointed out how Apple doesn’t rotate encryption keys at regular intervals. This makes it easy for attackers to make use of the same strategy to hack the device repeatedly.
Apple has been able to implement most if their suggestions, thereby eliminating most possibilities of an attack. The researchers still highly recommend that Apple replace its iMessage encryption protocol entirely.
[via Patently Apple]

