iPhone Hack Reveals Password in Six Minutes [Video]
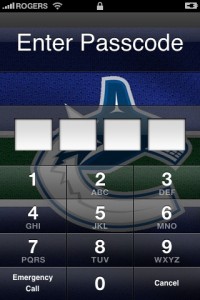
Protecting the contents of your iPhone with a passcode alone is not enough. German researchers were able to reveal an iPhone’s passcode in six minutes.
…the researchers first jailbreak the phone using existing software tools. They then install an SSH server on the iPhone that allows software to be run on the phone.The third step is to copy a keychain access script to the phone. The script uses system functions already in the phone to access the keychain entries and, as a final step, outputs the account details it discovers to the attacker.
The attack works because the cryptographic key on current iOS devices is based on material available within the device and is independent of the passcode, the researchers said. This means attackers with access to the phone can create the key from the phone in their possession without having to hack the encrypted and secret passcode.
Here’s a video of the attack:
No device is immune to an attack, but obviously it’s up to users to setup a passcode/password in the first place, and to always know where your iPhone is. Even with Find My iPhone, it can be easily disabled–if someone pops out your SIM card or turns on Airplane mode. At the end of the day, all companies need to work on security, especially Apple (remember this passcode flaw?).
What do you think of this video? Are you…scared?
[PC World]