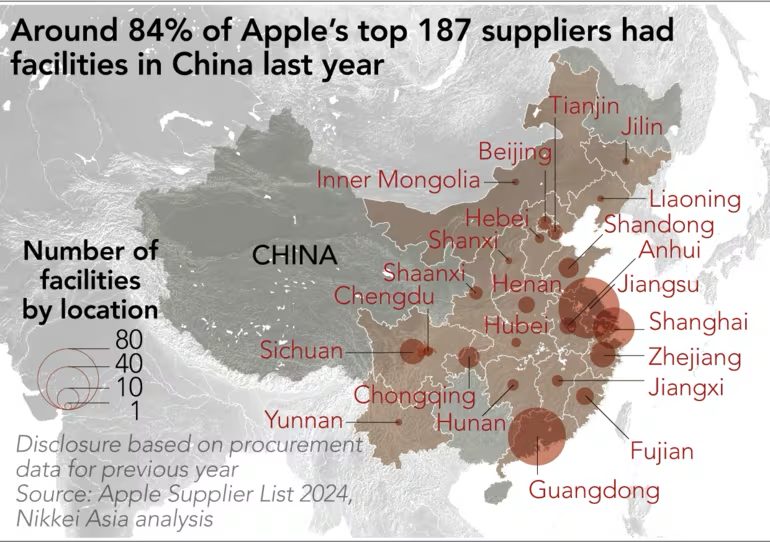
OS X 10.10.3 Failed to Patch Security Flaw “Rootpipe”, Former NSA Staffer Says
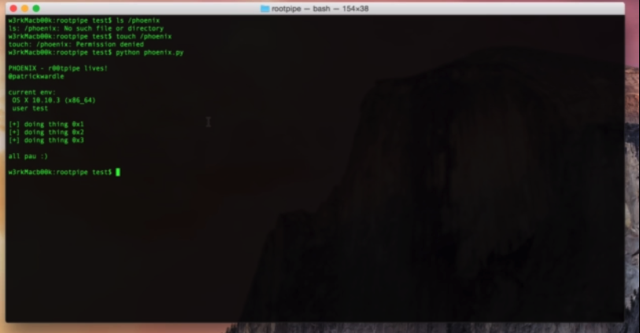
Apple claims the latest version of Mac OS X Yosemite has fixed a major security bug, dubbed Rootpipe. Not so fast, claims Synack security firm boss Patrick Wardle, a former NSA staffer, reports Forbes.
Rootpipe is a vulnerability in the operating system that grants a permanent backdoor to tens of millions of Apple Mac computers. It was discovered back in October 2014 by TrueSec security researcher Emil Kvarnhammar, who spotted that any OS X version below 10.10 is vulnerable to this flaw, which grants root access. However, it requires the hacker to obtain local privileges, via a malicious app, or an exploit in other software already sitting on the Mac.
Recently, a new OS X priv-esc vulnerabilty named ‘rootpipe’ was disclosed,” Wardle writes on his blog. “Apple attempted to patch the vulnerability in OS X 10.10.3, by adding access checks via a new private entitlement: com.apple.private.admin.writeconfig. (see @osxreverser’s excellent writeup for details). In theory this seemed a reasonable fix.
However, on my flight back from presenting at Infiltrate (amazing conference btw), I found a novel, yet trivial way for any local user to re-abuse rootpipe – even on a fully patched OS X 10.10.3 system. I the spirit of responsible disclosure, (at this time), I won’t be providing the technical details of the attack (besides of course to Apple). However, I felt that in the meantime, OS X users should be aware of the risk.
Wardle, however, raises the red flag: even Yosemite users running the latest version of the OS are vulnerable. A video of his code in action can be seen below.
Phoenix; RootPipe Reborn from patrick wardle on Vimeo.
Apple has yet to comment on the matter.