Unsecured Firebase Mobile Databases Reportedly Leaking Enterprise Data [u]
Thousands of iOS and Android mobile applications are exposing over 100 GBs of data via over 2,000 misconfigured Firebase databases.

Firebase is a Google product that contains a large number of services that developers can use in building both mobile and web-based apps. The service is very popular with Android developers, as it provides push notifications, cloud messaging, analytics, and a number of other backend services and APIs that they can use in their products. Developers that use the service obviously benefit from Google’s large-scale, high-performance systems.
According to a new report released this week by mobile security firm Appthority, a new “HospitalGown” threat variant is occurring when app developers fail to require authentication to Google Firebase databases.
The security researchers discovered the HospitalGown vulnerability last year, and it leads to data exposures not due to any code in the app but to the app developers’ failure to properly secure backend data stores (hence the name). The new Firebase variant exposes large amounts of mobile app-related data stored in unsecured Firebase databases.
Some of the potentially exposed data includes personally identifiable information, private health information, passwords, social media account information, cryptocurrency exchange private access tokens, vehicle license plate and registration numbers, and more.
“Enterprises are at significant risk from this vulnerability because 62% of enterprises have at least one vulnerable app in their mobile environment,” Appthority said in an updated blog post. “The vulnerable apps are in multiple categories, including tools, productivity, health and fitness, communication, finance and business apps.”
Among the findings is the fact that around 3,000 mobile iOS and Android apps – over 620 million Android downloads — are leaking data from 2,300 unsecured Firebase databases. Some of the app categories affected include tools, productivity, health and fitness, communication, cryptocurrency, finance and business apps, and more. Additionally, most enterprises are impacted: 62% of enterprises have at least one vulnerable app in their mobile environment.
“For context,” Appthority said, “Firebase is one of the most popular back-end database technologies for mobile apps but does not secure user data by default. Developers must secure all tables and all rows of data in order to avoid data exposure. And, unfortunately, it takes little effort for attackers to find open Firebase app databases and gain access to millions of private mobile data app records.”
Appthority has notified Google about the issue, providing them with a list of affected apps and Firebase database servers.
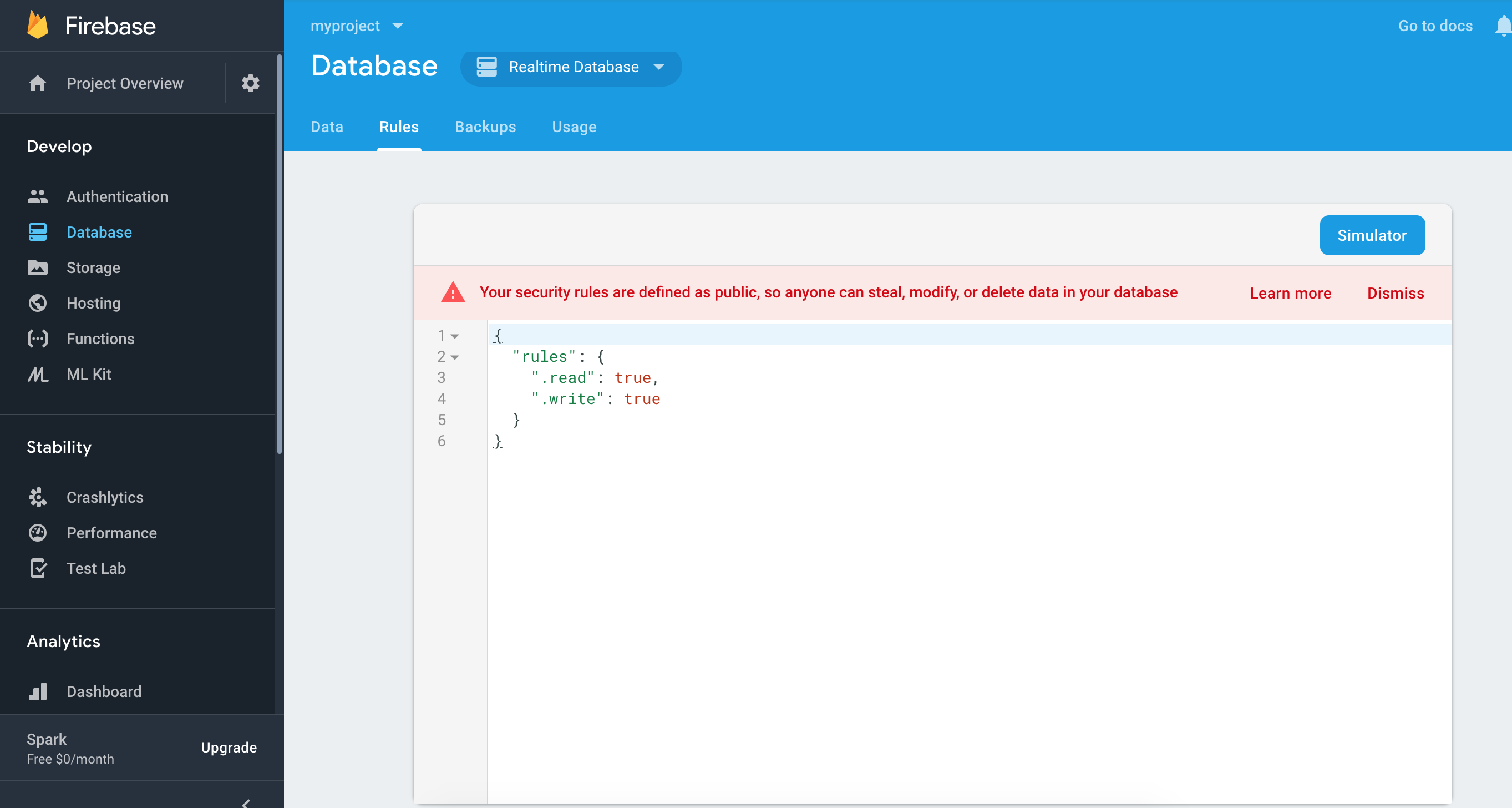
According to a Google spokesperson in an email to iPhone in Canada, they recommend to developers “Firebase security guides for Realtime Database, Firestore, and Storage are a good place for developers to start and provide detailed guidance on best practices. There’s even a pop-up in the Firebase console that tells developers when they’ve turned off security rules impacting their Firebase databases and that they are at risk for leaking data.”
Check out the screenshot below for reference:
Update June 30: Updated article with a statement from Google and updated quote from Appthority.