
Researchers Reveal Secret iMessage Exploit that Targeted iPhones
At the 37th Chaos Communication Congress in Hamburg, Germany, a team of cybersecurity experts, including Boris Larin from Moscow-based security firm Kaspersky, Leonid Bezvershenko, and Georgy Kucherin, disclosed a series of zero-day vulnerabilities in iPhones, exploited through iMessage.
This presentation, titled “Operation Triangulation,” marked the first public revelation of these vulnerabilities and their exploitation methods.
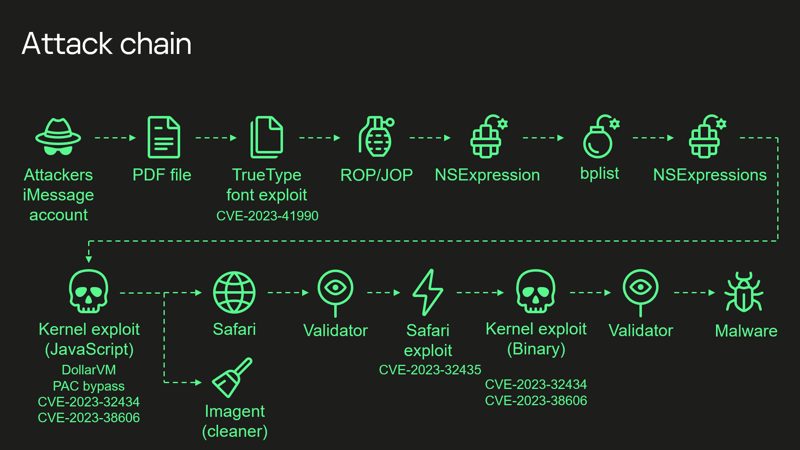
The attack, sophisticated in its execution, begins with a seemingly innocuous iMessage attachment. This attachment exploits CVE-2023-41990, a vulnerability in an undocumented TrueType font instruction, triggering a chain of events without any visible signs to the user. The exploit employs advanced techniques, including return/jump oriented programming and a multi-staged JavaScript exploit, to gain deep access to the device’s system.
A “zero-day exploit” is like finding a secret way into a computer program or system that nobody else knows about, not even the people who made the program, in this case, Apple. Because it’s a secret, there’s no protection against it yet. The name “zero-day” means that the makers of the program have had zero days to fix the problem, because they just found out about it.
Key to this attack is the exploitation of four zero-days, designed to be effective up to iOS 16.2. The researchers detailed how the attack manipulates the JavaScriptCore debugging feature and an integer overflow vulnerability (CVE-2023-32434) to gain read/write access to the entire physical memory of the device at the user level. This approach allows the attackers to bypass the Page Protection Layer (PPL), a security feature intended to protect against such intrusions.
The Triangulation cyber espionage tool/malware turns out to be extremely advanced/fascinating. Certainly the ~most impressive piece in 2023, perhaps among the most impressive (known) cyber espionage tools in history? https://t.co/nP6Ev9oGuZ pic.twitter.com/noCwMPlgzA
— Lukasz Olejnik, Ph.D, LL.M (@lukOlejnik) December 27, 2023
It’s worth noting that these exploits have already been patched by Apple’s iOS software updates from this summer, with iOS and iPadOS 15.7.8 for older devices and 16.6.
“The exploit’s sophistication and the feature’s obscurity suggest the attackers had advanced technical capabilities,” said Larin in an email to ArsTechnica. “Our analysis hasn’t revealed how they became aware of this feature, but we’re exploring all possibilities, including accidental disclosure in past firmware or source code releases. They may also have stumbled upon it through hardware reverse engineering.”
The presentation highlighted the exploit’s ability to support both older and newer iPhone models, including a Pointer Authentication Code (PAC) bypass for recent models. The exploit’s complexity is further evidenced by its use of hardware memory-mapped I/O (MMIO) registers, a method that was mitigated as CVE-2023-38606.

