
Chinese Government-Linked Hackers Caught Bypassing 2-Factor Authentication
Dutch cyber-security firm Fox-IT has recently found evidence suggesting a Chinese government-linked hacking group dubbed ‘APT20’ has been bypassing two-factor authentication (2FA) in a recent wave of attacks, ZDNet is reporting.
Researchers say the group’s primary targets were government entities and managed service providers (MSPs) from fields such as aviation, healthcare, finance, insurance, energy, and gambling.
The hackers used web servers as the initial point of entry into a target’s systems, focusing on an enterprise application platform called JBoss, which is often found in government and large corporate networks.
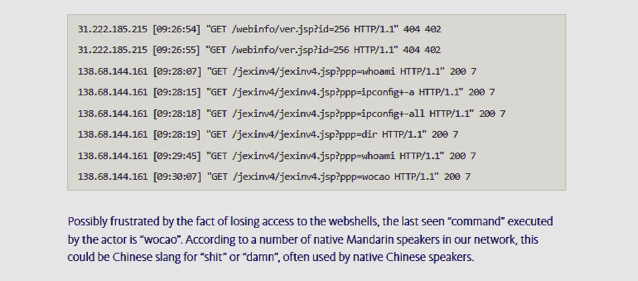
According to the researchers, APT20 used vulnerabilities to gain access to these servers, install web shells, and then spread through the victim’s internal systems:
But this wasn’t the thing that stood out the most in all the attacks the Dutch security firm investigated. Fox-IT analysts said they found evidence the hackers connected to VPN accounts protected by 2FA.
How they did it remains unclear; although, the Fox-IT team has their theory. They said APT20 stole an RSA SecurID software token from a hacked system, which the Chinese actor then used on its computers to generate valid one-time codes and bypass 2FA at will.
More information on these attacks can be found at this link.

