
Unpatched iOS 13 Bug Prevents VPNs from Encrypting All Traffic
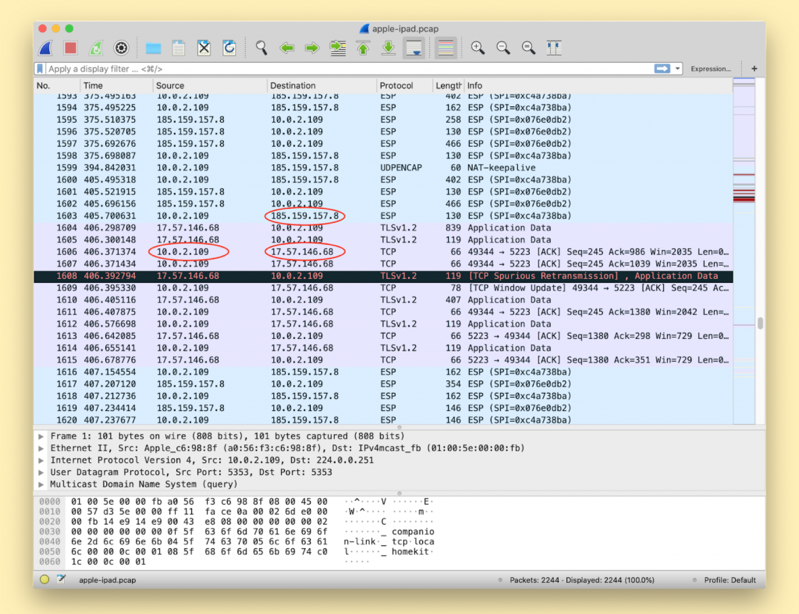
Image shows: 10.0.2.109 = iOS device’s IP address; 185.159.157.8 = ProtonVPN server; 17.57.146.68 = Apple-owned IP address; the Apple-owned IP address connection should not be on when a VPN is enabled
ProtonVPN has published details of how a bug in iOS 13.3.1 and higher (including the latest iOS 13.4) prevents a virtual private network (VPN) from encrypting all traffic:
A member of the Proton community discovered that in iOS version 13.3.1, the operating system does not close existing connections. (The issue also persists in the latest version, 13.4.) Most connections are short-lived and will eventually be re-established through the VPN tunnel on their own. However, some are long-lasting and can remain open for minutes to hours outside the VPN tunnel.
In other words, some connections to the web do not connect to your VPN, withs one staying unencrypted for up to hours.
According to ProtonVPN, “the VPN bypass vulnerability could result in users’ data being exposed if the affected connections are not encrypted themselves (though this would be unusual nowadays).”
With unencrypted connections, a user’s IP could leak and be seen by an attacker, revealing the IP address of servers they are connecting to. Also, servers you’re connecting to could also see your actual unmasked IP, instead of that provided by your VPN.
ProtonVPN says they have informed Apple of this flaw, but published details now to let users protect themselves. They said Apple has “acknowledged the VPN bypass vulnerability and is looking into options to mitigate it.”
“Those at highest risk because of this security flaw are people in countries where surveillance and civil rights abuses are common,” adds the Swiss-based company.
There is no workaround for this iOS bug, says ProtonVPN, because “iOS does not permit a VPN app to kill existing network connections.”
But ProtonVPN says they have come up with a workaround that looks “to be almost as effective”.
Here’s how to protect yourself from this iOS 13.3.1 and iOS 13.4 VPN bypass vulnerability:
- Connect to any ProtonVPN server.
- Turn on airplane mode. This will kill all Internet connections and temporarily disconnect ProtonVPN.
- Turn off airplane mode. ProtonVPN will reconnect, and your other connections should also reconnect inside the VPN tunnel, though we cannot guarantee this 100%.
The discovery of this iOS VPN flaw was found by security consultant @cibersaludables.
ProtonVPN offers a free VPN, plus paid options starting from $4 USD per month.

