iOS Sandbox Flaw Puts Enterprise Customers at Risk
On August 13, Apple pushed out iOS 8.4.1. While the accompanying release notes mainly focused on iTunes bug fixes, the update also patched a major iOS security flaw that had allowed hackers to get access to enterprise credentials used by apps for corporate server access.
The flaw was first noticed by mobile security firm Appthority, which immediately notified Apple. Now that the vulnerability has been fixed, Appthority has stepped out and published the details of their findings that prompted Apple to come up with an instant fix to safeguard its expansion into the enterprise market.
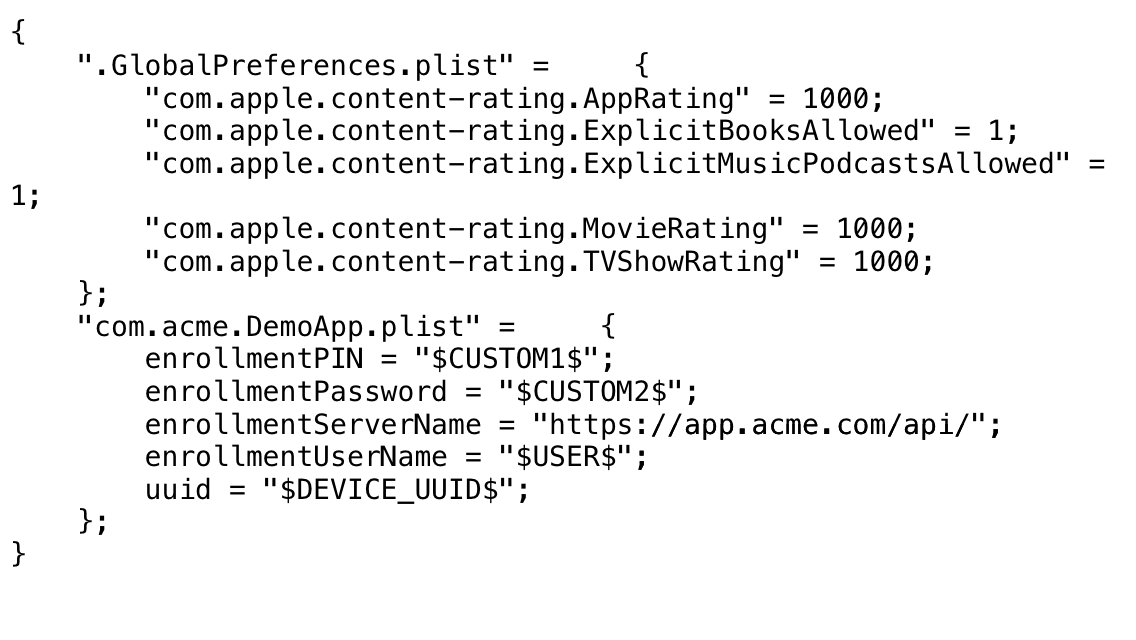
In a blog post, Appthority explains that the unknown flaw affects MDM clients as well as apps which are distributed through an MDM (Mobile Device Management) Managed App Configurations settings.
Considering that IT departments commonly send the credential and authentication information along with the managed app binary for installation on mobile devices to “auto-fill” account setup, it’s convenient and fast.
Not so fast, says Appthority. The flaw within iOS, which they named “Quicksand”, allowed a mobile app or the MDM vendor app itself to monitor this sensitive data, and since the credentials are stored in a world-readable format, malicious apps exploiting this vulnerability can review this sensitive info.
Of course, now that this iOS flaw vulnerability has been patched, enterprise customers can sit back and relax. There is a problem, though: The vulnerability affects all iOS users who haven’t yet updated to iOS 8.4.1, and according to their latest data, about 70% of users have not. So, if you haven’t already done so, you may want to update your iPhone.