Report Says 1,500 iOS Apps Vulnerable to Man-in-the-Middle-Attacks
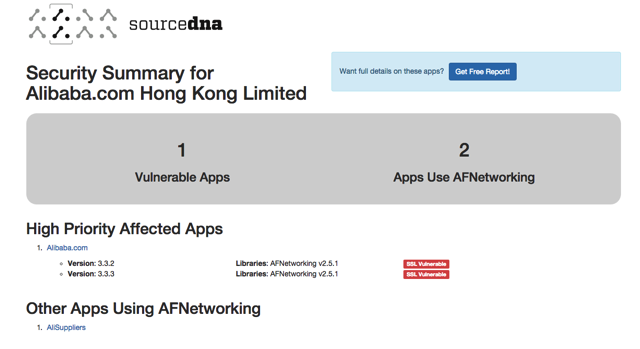
Roughly 1,500 iOS apps for iPhone and iPad contain an HTTPS-crippling bug which makes them vulnerable to man-in-the-middle attacks, and allows hackers to intercept encrypted passwords and other sensitive information, new research signed by SourceDNA reveals (via Ars Technica).
While iOS is a secure platform, apps can cause unwanted headaches for users, due to poor security measures. The problem with apps such as Citrix OpenVoice Audio Conferencing, alibaba.com mobile app, and Revo Restaurant POS app is that they use an older version of an open-source code library called AFNetworking which allows developers to drop network capabilities into their apps.
“The issue occurs even when the mobile application requests the library to apply checks for server validation in SSL certificates,” researchers Simone Bovi and Mauro Gentile wrote in a blog post published in late March. They went on to say that they analyzed one app running AFNetworking 2.5.1 and found alarming results. “We tested the app on a real device and, unexpectedly, we found that all the SSL traffic could be regularly intercepted through a proxy like Burp without any intervention!” (Emphasis is theirs.)
As Ars Technica points out, AFNetworking maintainers have fixed a security flaw by releasing version 2.5.2, but version 2.5.1 – the version the aforementioned apps are using – contains the HTTPS-crippling bug, and leaves these apps and its users vulnerable to hacker attacks.
After scanning a million of the 1.4 million apps available in the App Store, SourceDNA identified vulnerable apps in the top 5,000 free titles. SourceDNA also released a search tool that lets you check to see if specific apps are vulnerable. You can do this by hitting this link.