
Deceptive Google-Verified Ad Leads to Fake Keepass Website
Google has unwittingly hosted a malicious ad that appears to have effectively deceived even security-savvy users, as reported by Malwarebytes (via ArsTechnica).

The deceptive ad mimics a promotion for the open-source password manager, Keepass, giving no indication of its fraudulent nature.
This is particularly problematic because the ad is on Google, a platform known for its ad vetting process.
What makes this ruse even more convincing is that clicking on the ad takes users to a site that seemingly represents the legitimate Keepass site, visible as “ķeepass[.]info” in the address bar.
However, upon closer inspection, it is evident that this site is a deceptive replica. The address “ķeepass[.]info” is actually an encoded form of “xn--eepass-vbb[.]info,” a site responsible for distributing a malware family known as FakeBat.
According to Jérôme Segura, head of threat intelligence at Malwarebytes, users are first fooled by the Google ad’s authenticity and then again by the lookalike domain.
Data from Google’s Ad Transparency Center reveals that these misleading ads have been running since Saturday and last appeared on Wednesday.
These ads were paid for by an entity called Digital Eagle, which Google claims to have verified.
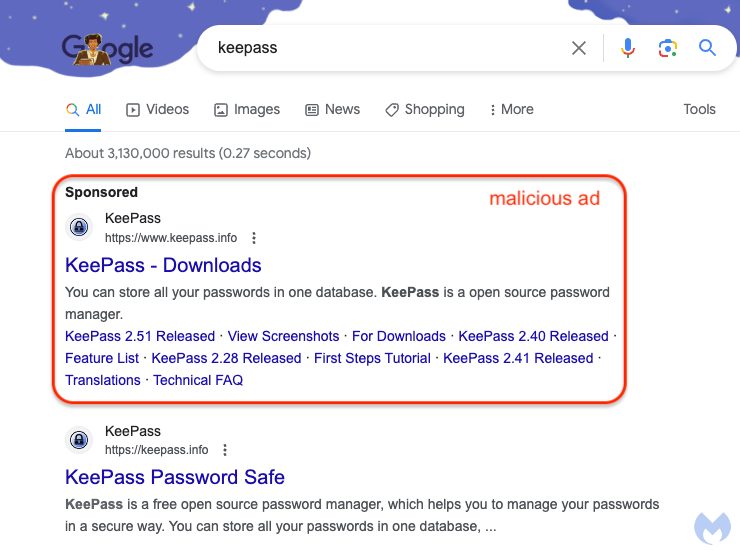
While Google has a history of promptly removing fraudulent ads upon reporting, this incident highlights the challenge of detecting malvertising and punycode-encoded URLs.
The use of punycode allows Unicode characters to be represented as standard ASCII text, making it challenging for users to discern the deception.
Even with careful scrutiny, it’s easy to overlook the subtle comma-like figure below the “k.”

